For added security, students can use their cell phones to verify their identity through Duo Protection. To set it up, click register on this page.
Ball State University students receive over a million collective spam emails a day, said Tobey Coffman director of information security.
Many of these spam emails are trying to phish Ball State students, Coffman said. Phishing, or an attempt to gain confidential information like passwords, is a growing problem for universities according to an Inside Higher Ed article.
“This is a very, very common problem everywhere,” Coffman said. “Universities probably get targeted more than other businesses because we are a more open environment.”
Since September 12, phishing campaigns were sent to Ball State students, Coffman said.
“We error on the side of blocking less because we don’t want something that is legitimate to not get to you,” Coffman said. “Every email you receive, make sure you take a really close look at it.”
Coffman said while phishing emails have changed over the years, they have been around as long as emails.
“They are always evolving to find the next thing that people aren’t expecting,” Coffman said. “Instead of someone mugging you on the street, you have someone trying to get electronic credentials to mug you online.”
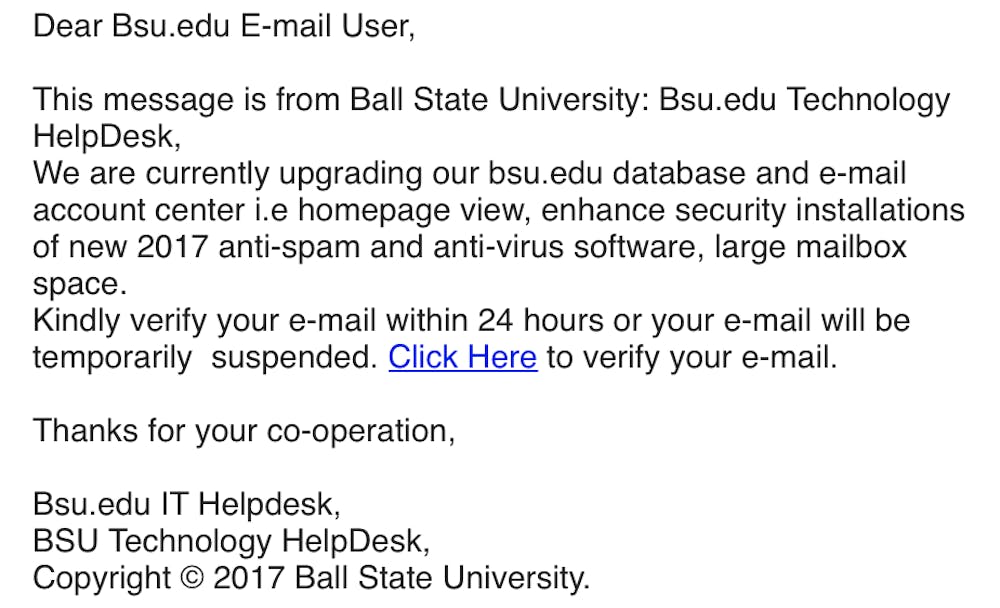
Ball State prevents phishing through several customizable Microsoft filters. Primarily, it puts obvious fraud emails in spam, Coffman said. Obvious emails include statements such as “Dear sir” or severe spelling errors.
Additionally, the Office of Information Technology (OIT) at Ball State adds another layer of protection through Microsoft called Advanced Threat Protection (ATP).
ATP allows Microsoft to check a website out before users visit the site. It lets users know if the website has anything suspicious and then gives users the choice to continue to the website.
ATP also puts warnings at the top of suspicious emails. This is to help students better evaluate an email, Coffman said.
Students should look for extended validation certificates on a company’s website. These certificates act as validation that the website is real, similar to a validated celebrity on Twitter, Coffman said. A website has this certificate if its URL is green while a user is on the site.
URLs are key to preventing phishing because they can show a certificate and suspicious email addresses.
Students should also be suspicious when emails request a user to click on links that ask for a password.
“To create a sense of urgency, the scammer will try to trick the student into believing something bad will happen – their account will be disabled, they will run out of space, or something along these lines,” said Loren Malm interim vice president of information technology. “If you get any email indicating you need to click on a link and enter your username and password, that email should be either deleted or verified by contacting the Helpdesk.”
If students do enter their password, they should never use the password again. Scammers will keep that login and password information and try it on various sites, Malm said.
Ball State is 69th most common email domain on the dark web, according to the Digital Citizens Alliance’s 2017 study.
“Criminals may use the stolen password for accessing the student’s information for more damaging purposes such as stealing information to file fraudulent tax returns or to commit other forms of identity theft,” Malm said.
Contact Liz Rieth with comments at ejrieth@bsu.edu or on Twitter at @liz_rieth.